Step 2: Gateway Installation
Install and configure SDA Glue on your gateway hardware with step-by-step instructions for Linux, Windows, Docker and proxy environments.
With your Gateway and devices configured in the SDA Console, the next phase involves installing the SDA Glue service on your chosen gateway hardware. This installation process differs between Linux and Windows systems, but both approaches follow the same fundamental principle: downloading and configuring a service that runs continuously in the background, ready to establish secure tunnels on demand.
Installation
The installation process consists of two main phases:
Install the SDA Glue and dependencies in the target system.
Configure the service with unique credentials from the SDA Console, that authenticate a specific Gateway.
Before beginning the installation, ensure you have administrative privileges on your target system. The installation process requires elevated permissions to install the system service. For Linux, you'll need sudo access. For Windows, you'll need to run PowerShell as an Administrator.
The installation process can accommodate proxy environments, but requires additional configuration steps that we'll detail in each platform-specific section.
Linux
To install SDA Glue on a Linux system with direct internet access, execute the following command in a terminal:
curl -sSL 'https://api.eu1.sdaconsole.io/glue/v1/install/script/linux' | bash -This command uses curl to securely fetch the installation script directly from SDA's API endpoint and pipes it to bash for immediate execution. The -sSL flags ensure the transfer is silent, shows errors if they occur, and follows any redirects securely.
Linux with Proxy
When your Linux system requires internet access through a proxy server, you must configure the appropriate environment variables before running the installation script. Set the http_proxy and https_proxy environment variables in your current bash session:
Replace the proxy URL with your actual proxy server details, including authentication credentials if required by your network configuration.
Docker
Docker provides an alternative deployment method that offers consistency across different host systems and simplified management through containerization. The SDA Glue Docker image is based on Debian and includes all necessary dependencies pre-configured, eliminating the need for manual compilation or dependency management.
To deploy SDA Glue using Docker, run the following command with the required network capabilities:
This command creates a persistent container named "glue" that will automatically restart if it stops unexpectedly. The volume mount preserves your gateway's configuration and authentication data between container restarts or updates.
It also forwards the container port 8080 to the host port 8081, which runs the Glue web server for setting up the application. You can then access it with http://localhost:8081/.
For comprehensive Docker deployment guidance, including advanced networking configurations, troubleshooting steps, and production deployment best practices, visit the complete documentation:
Windows
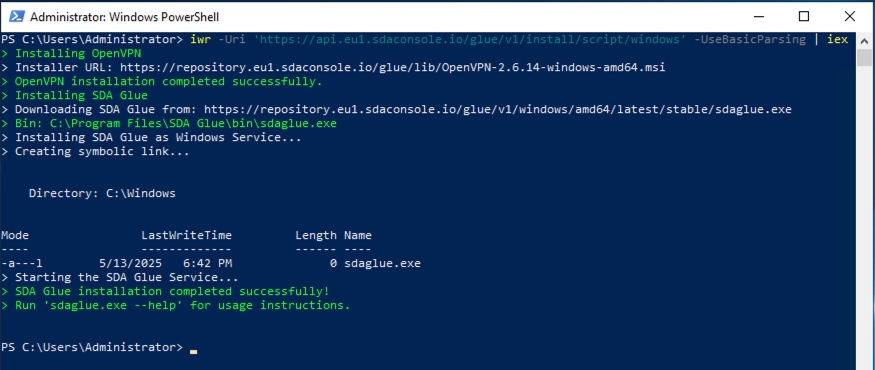
Open PowerShell as an Administrator by searching for "PowerShell" in the Windows search bar, right-clicking on the result, and selecting "Run as administrator". Once you have an elevated PowerShell session, execute the following command:
This PowerShell command uses Invoke-WebRequest (abbreviated as iwr) to fetch the installation script and pipes it to Invoke-Expression (abbreviated as iex) for immediate execution. The -UseBasicParsing parameter ensures compatibility across different Windows versions and configurations.
Windows with Proxy
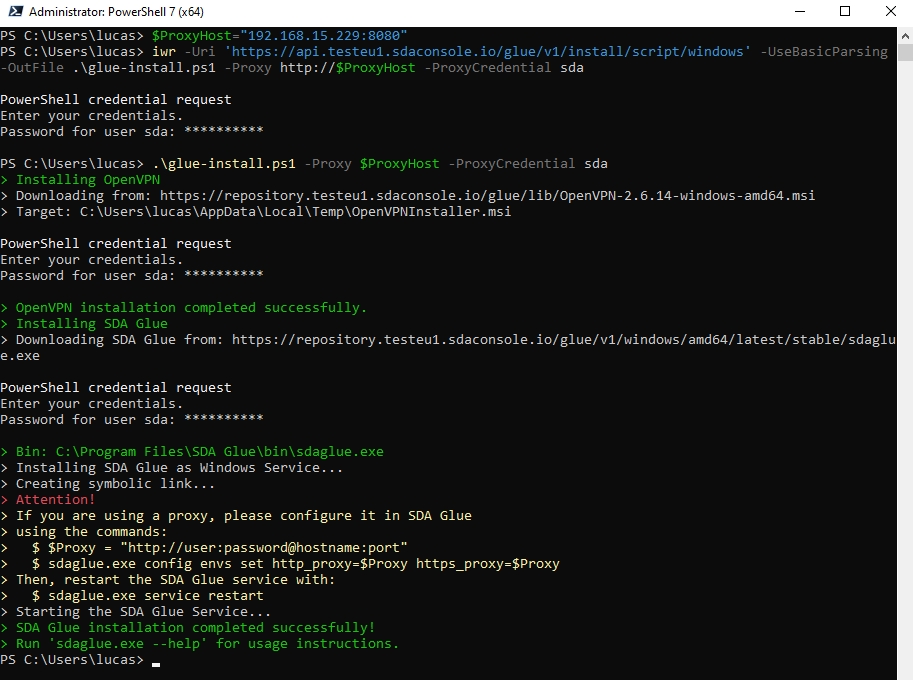
When your Windows system operates behind a proxy server, the installation process requires a two-stage approach. First, you'll configure the proxy settings and download the installation script. Then, you'll execute the script with the appropriate proxy configuration.
Begin by setting PowerShell variables for your proxy configuration:
Note the important distinction in proxy URL formatting: the Invoke-WebRequest command requires the full URL scheme (http://proxy.company.com:8080), while the installation script expects only the hostname and port (proxy.company.com:8080).
Authentication and Login
After successfully installing the SDA Glue software, you must authenticate your physical gateway with the SDA Cloud services. This authentication process uses unique credentials generated by the SDA Console for your specific gateway. These credentials consist of a short gateway identifier and a one-time password that rotates periodically for enhanced security.
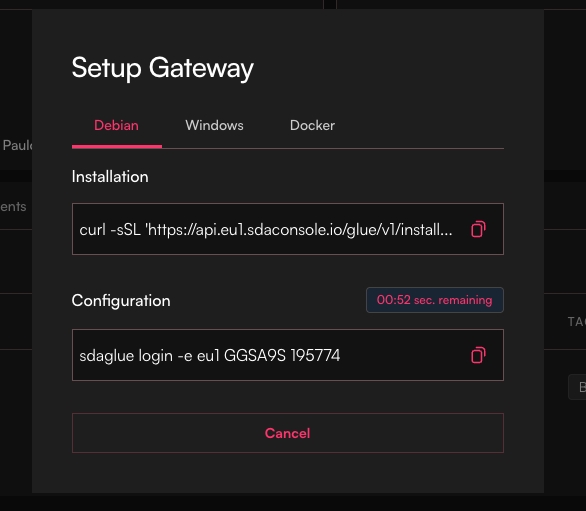
Return to the SDA Console and locate the second command in your gateway's setup dialog. This command will look similar to the following examples:
Linux
Docker
Windows
The command structure includes the -e eu1 flag specifying the European region endpoint, followed by your gateway's unique identifier (such as G1ABCD) and the one-time password (such as 123456). These values are specific to your gateway and will differ from the examples shown.
Service Status
After completing the installation and authentication process, verify that the SDA Glue service is running correctly on your system.
Linux
Check the service status using systemd commands:
To monitor live log output and troubleshoot any issues:
Docker
The service logs can be retrieved from Docker containers with:
Windows
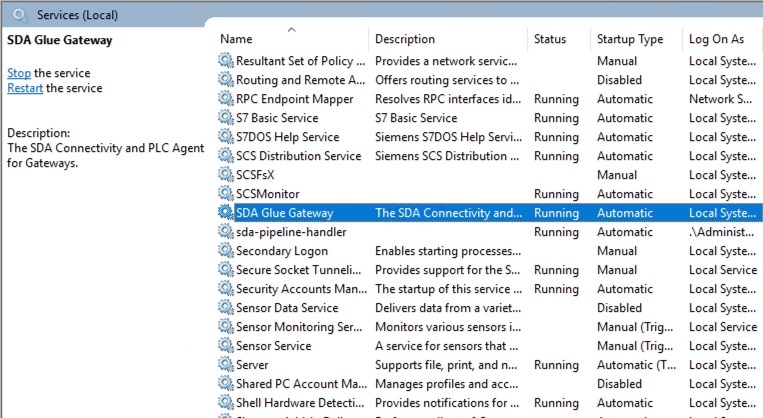
You can verify the service through the Windows Services application. Search for "Services" in the Windows search bar and look for "SDA Glue" in the service list. The service should show as "Running" with a startup type of "Automatic".
Windows Services produce Event Logs, that can be accessed on the Event Viewer, under Windows Logs → Application. Use the search bar to open the Event Viewer.
Configuration
SDA Glue allows you to modify its behaviour to work optimally within your specific network environment. These configuration adjustments ensure reliable connectivity regardless of your industrial network's unique characteristics, whether you're dealing with proxy servers, firewall restrictions, or different communication protocols.
We use environment variables to control the service. Configuration changes require a service restart to take effect. Environment variables keep the same configuration parameter naming convention, but it uses the GLUE prefix and is separated by underscores:
View current configuration parameters:
Setting parameters:
Retrieving parameters:
Restart service after changes:
MQTT Transport Protocol
One of the most important configuration decisions involves choosing how your gateway communicates with the SDA Cloud services. SDA Glue supports two transport protocols, each designed for different network environments:
MQTT
SSL / TCP
443
Standard networks with direct internet access
MQTT over WebSocket
WebSocket Secure (TCP)
443
Networks with transparent proxies or SSL inspection
For WebSocket transport:
For standard MQTT transport:
Proxy Server
When your network requires all internet traffic to flow through a specific proxy server, SDA Glue must be configured with the proxy details to establish connections with SDA Cloud services. This is particularly common in corporate environments where direct internet access is restricted for security purposes.
Proxy addresses follow the standard format: scheme://username:password@hostname:port
Scheme: Usually
http://orhttps://Username/Password: Authentication credentials (if required by your proxy)
Hostname: The proxy server's address
Port: The proxy server's port number
You must configure both HTTP and HTTPS proxy settings to ensure complete coverage of SDA Glue's communication needs.
Linux
Docker
Windows
Common Issues
Corporate Network with Transparent Proxy
Problem: Gateway connects initially but frequently disconnects or shows unstable connectivity.
Solution: Switch to WebSocket transport protocol.
Restrictive Firewall Environment
Problem: Gateway cannot establish initial connection to SDA Cloud services.
Solution: Configure WebSocket transport and verify that outbound HTTPS connections are allowed on port 443.
Authenticated Proxy Server
Problem: Gateway cannot connect through corporate proxy requiring authentication.
Solution: Configure both proxy settings with proper authentication credentials and restart the service.
With these configuration options properly set, your SDA Glue service will adapt to your network environment and maintain reliable connectivity to the SDA Cloud services, enabling secure access to your industrial devices.
Last updated
